Introduction
As digital networks grow they can become congested and less secure. By dividing network attached resources into smaller groups, physically and/or logically, congestion is reduced and security increased on each individual segment when clients and servers are properly grouped into more self-contained boundaries of clients being matched to frequently used service providers. In order to subnet an IP-based network, the allocation of IP addresses to be used on each segment of the subnetted network needs to be determined. Many factors affect this determination starting with the available number of IP addresses currently available to the organization.
If companies had to rely only on the available and costly public IP v4 addresses they have available to them, adding clients and servers to their network internally would be very expensive. Luckily there are a set of private IP v4 addresses available which are not used on the Internet. This is good and bad. Good in that the available private IP addresses ranges give companies the ability have lots of devices connecting to their networks internally. Bad, because those resources can't use those private addresses to communicate outside the company network. Actually, it's not all that bad because there is a technology called Network Address Translation, available on most routers, which can share a companies limited public IP addresses with the internal devices using the private addressing scheme.
More about NAT in a later lecture, for now we a focused on identifying what range of IP addresses are available for internal use and how to organize those addresses into smaller groupings of client/servers based on usage, for reducing congestion and adding security to each segment.
The Subnet Mask
In IP-based implementations a subnet mask is used in conjunction with a device's IP address to determine the network the device can connect to and the unique value that represents the device itself.
A subnet mask has two purposes in life:
- To identify which
bits in a device's IP address represent its network address by
separating, masking, the host address portion of
the IP address using a Boolean algebraic process known as
anding.
- To compare the destination IP address of a message to the host's (the sending device's)
source IP address and determine if the destination device is
local (on your network) or remote (located on another subnet on your local intranet or out on the Internet). The results of this analysis will determine the destination MAC address of the message you're sending, which will be either the MAC address of a
local (on your network) computer or the MAC address of your default gateway (router
attached to your network) which will forward your message to another network in order for it to reach its
final destination.
An IP address is comprised of two constituent parts, the network
address and the host address.
The network portion of a device's IP address identifies the
specific network the device is attached to. The network
address is a unique value which identifies the specific Local Area
Network (LAN) the device is connected to.
The host portion of an IP address is a
unique value for a specific device which cannot be duplicated by any other
device connected within the same LAN.
Like a mailman would use your street name or zip code to help identify which neighborhood your house is located in
(the network). The host portion identifies the device within the network, like your house number is unique to the street you live on. Only your house has that number on your street. There can be the same house number on
a house on another street, but only your house has that number on your street.
So when looking at a device's IP address and its subnet mask, how
do we know what its network address is and what
its host address is? Well that is the skill you
are going to learn here, how to identify where the network portion
ends and the host portion begins, what a device's network address is
and what its host address is by just looking at an IP address and
its subnet mask.
Since this division between the end of the network portion of an IP
address and the beginning of the host portion of the IP address can take
place at any one of an IP address' 32 bits, we must view the IP address and
its corresponding mask at the binary level, just as a computer sees it.
The subnet mask completes both tasks (1 and 2 above) by using a Boolean algebra process called "Anding". The subnet mask is "anded" to the source IP address and then the subnet mask is "anded" to the destination IP address. When you "and" two binary numbers you have these four possible results:
- 0 "and" 0 = 0
- 0 "and" 1 = 0
- 1 "and" 0 = 0
- 1 "and" 1 = 1
Using this methodology the subnet mask is able to separate out the network portion of an IP address for both the source and destination IP address. It then compares the two network addresses to determine if the destination is local or remote. So wherever there are 1's in the subnet mask means the corresponding bit in the IP address is part of the network address.
Example - if your IP address is 192.168.1.24 and your mask is 255.255.0.0, when you convert the mask to binary the 255's becomes a string of eight 1's. Simply put, wherever we see a 255 in the subnet mask the corresponding octet in the IP address is the network portion of the IP address and the zeros represent the host portion of the IP address. In this example then 192.168.0.0 is the network where you will find the host 1.24.
192.168.1.24 in binary looks like this:
11000000.10101000.00000000.00011000 and the subnet mask 255.255.0.0 in binary looks like this:
11111111.11111111.00000000.00000000 if you "and" the two binary numbers together the result is this:
11000000.10101000.00000000.00000000 which, when converted to decimal looks like this:
192.168.0.0 which is the network ID of where the IP host is located.
The 1's in a subnet mask will always be contiguous starting from left to right. The binary value of the mask in the example above is 11111111.11111111.00000000.00000000. You'll never see a mask that has non-contiguous 1's in it like 11001110.00111111.00001111.11110000. So, there are only eight possible masks that can be created in any one octet.
10000000 = 128
11000000 = 192
11100000 = 224
11110000 = 240
11111000 = 248
11111100 = 252
11111110 = 254
11111111 = 255
(see Subnetting Table for a better visualization of why these are the only subnet mask values you will ever see).
When you subnet an existing network you have to add 1's to the existing subnet mask so that an IP host (computer, router, etc.) can correctly detect if another IP host is on the same subnetwork it is, or if they are on different subnetworks from each other. If you think about it what you're really doing is extending the network address from its original number of bits to allow us to create subnetworks within a single, larger network. This will also have the affect of reducing the number of hosts that can be add to a subnetwork. Each time we borrow a "host" bit from the host portion of the IP address/subnet mask to use as a network bit we have one less bit available for use as a host bit, thereby reducing the total number of physical hosts that can be added to each subnetwork. In other words, the more subnetworks you have, the fewer hosts you will have per subnetwork.
You can determine the number of hosts that you can have on a subnet by taking 2 to the power of the number of 0's there are in the subnet mask.
Example - If our mask is 11111111.11111111.11111111.00000000 then raise 2 to the power of 8 (eight zeros in the mask) = 256 then subtract 2 because you can have a host value where all the bits are 1's nor can you have a host value where the bits are all 0's. For instance, using the mask above you couldn't have an IP address that is 192.168.1.0 because that is the reference to the subnetwork; another way to say it is that the host portion of the IP has to be at least 1. And, you can't have an IP address that is 192.168.1.255 because 255 is all 1's and that is a reserved address used too at the network layer of the OSI model to broadcast messages to all IP hosts on the same subnet. So 2 to the power of the number of the 0's (8) is 256 minus the two unusable IP addresses leaves us with the ability to assign 254 valid IP addresses to IP hosts on our each of the subnets that use the subnet mask 255.255.255.0.
To determine how many bits you need to increase you mask by you need to know how many subnetworks you want to create. This is where the subnet table comes in handy; let's say you want to create three subnetworks and your current subnet mask is 255.255.0.0. When you look at the subnet table look for the column that has the decimal value that is greater than the number of subnetworks you're creating by at least 2. In our example 3 subnets + 2 = 5, so we're looking for the column equal to or greater than five. 8 is the first column that meets that criteria. Then determine how many bits does it take to make the number; in other words, 2 to the power of what makes 8? Well two to the power of 3 makes 8, so we need to add three 1's to our mask. That means our new mask will be 11111111.11111111.11100000.00000000 or in decimal 255.255.224.0.
It helps if you can start seeing the numbers in binary, because that's the only way a computer sees them. It simply "ands" the first bit in the subnet mask to the first bit in the IP address, and then the second bit of the subnet mask is "anded" to the second bit in the IP address, and so on and so forth. It first "ands" the source address and then the destination address. Then it compares the two results.
Next, using ARP the IP host will try to find either the MAC address of a local IP Host or the MAC address of the Default Gateway (router) that can forward the message to a remote destination. The computer then tells the NIC to frame the message it wants to send. At the datalink layer the destination MAC address will either be a that of a local computer (any IP host attached to the same switch as the sender), or it will be the MAC address of the router, or all twelve digits of the MAC address will be the hexadecimal value "F" which is the "broadcast" address at the Data Link layer. A hexadecimal "F" in binary is four 1's, so broadcast at the Data Link layer is a sequence of 48 1's. When a MAC layer broadcast is sent as the destination MAC address, all IP hosts on the same subnetwork will process the Data Link header of the message and hand-off the remainder of the encapsulated headers and data to the Network layer for processing.
Learning Resources
Subnetting Lecture
This lecture covers numbering systems, binary to decimal conversion, and the 5 steps used to subnet a network.
Learning Tools
Practice Using These Documents!
Subnetting Table
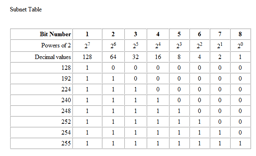
Use the Subnetting Table above to assist you
with your subnetting calculations.
Subnetting Practice Form

Note: Your actual Skills #2 Subnetting Form will require four subnets. The only change from your practice form will be the network address and the
prefix (CIDR) value.
More On Subnetting
If you are still having problems understanding subnetting read this document on subnetting.