Overview
The first layer of the OSI Network Reference Model, the Physical layer, is responsible for the establishment, maintenance, and termination of the physical connections between communicating devices. There is no data recognition at the Physical layer only streams of bits.
The Physical layer does not define the specifications for media and connectors. These specifications are sometimes referred to as layer 0.
Point-to-Point Data Transmission Technologies
The most basic data communication technologies are those used to directly connect two devices. The connections can be used to connect a computer to peripheral devices such as modems, scanners, PDAs, and so on, or as the basis for a directly connected computer-to-computer data connection.
Serial Transmission Standards
Serial transmission is the basis of most data communication between computing
devices peer-to-peer, or computing device and peripheral device such as
a printer. There are several different serial communication standards available for use in modern day computers, including RS-232, USB, and IEEE 1394 (Firewire).
RS-232
The RS-232 protocol is currently the most commonly used serial standard for modem communication. Standardized by the Electronics Industry Association (EIA), RS-232 is currently in its third release (RS-232-C). The
prevalence of RS-232 in the PC marketplace is so great that the term serial port has come to mean an RS-232 serial connection.
RS-232 is officially limited to 20 Kbps for a maximum distance of 50 feet. In reality, depending on the type of media being used and the amount of external interference present - RS-232 can be transmitted at higher speeds and/or over greater distances. However, modern hardware typically
supports speeds up to 115 Kbps using 16550 family UARTS.
RS-232 uses electrical signals to transmit the ones and zeros of the digital datastream. The RS-232 standard defines voltages of between +5 and +15 volts DC on a given pin to represent a logical zero, otherwise known as a space, and voltages of between -5 and -15 volts DC to represent the logical ones, otherwise known as a mark.
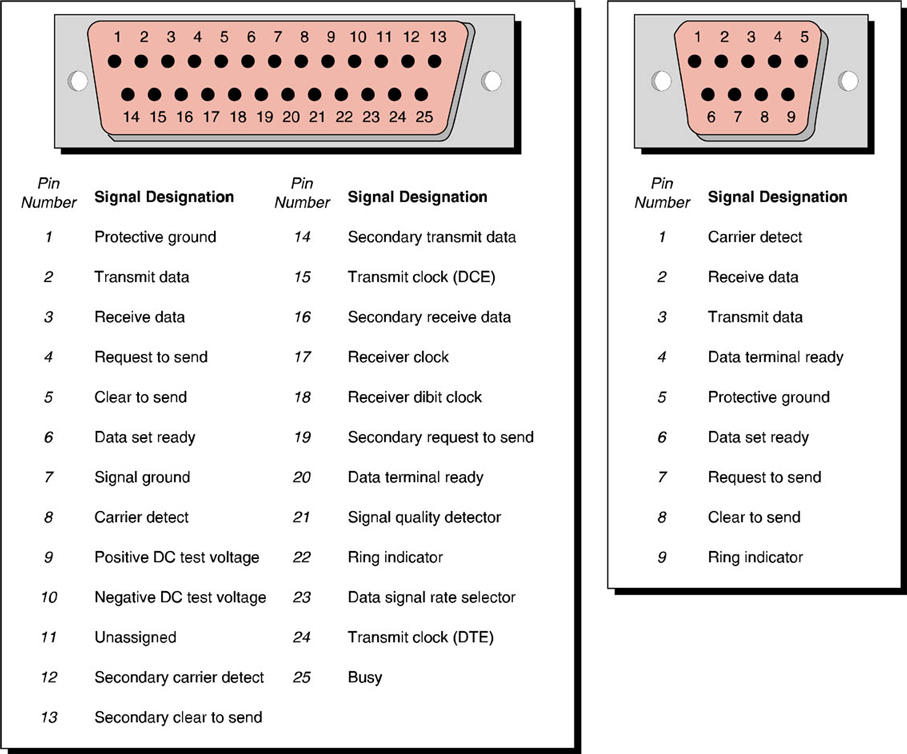 Figure 1: RS-232 25-pin and 9-pin pinout diagrams.
Figure 1: RS-232 25-pin and 9-pin pinout diagrams.
Physical Interfaces vs. Transmission Protocols
It is important to distinguish between those standards that describe the connectors or physical interfaces that are used to connect appropriate cables to a computer's physical ports, and standards that describe the electrical characteristics, or transmission protocols used;
also referred to as signaling.
RS-232 Cables
To connect devices via RS-232, a multi-wire cable must be used. The cable has several small, insulated wires within an outer jacket. Each signal to be carried, or RS-232 pin to be supported, requires its own individual inner wire.
The number of signals that must be transmitted across an RS-232 connection between two devices will depend on the software used. The number of signals required can vary from as few as two for one-way communication to twelve for a full-duplex modem connection.
DCE vs. DTE
The original application of RS-232 was to connect computing devices to modems. To make this "standard" solution easier, two classifications of RS-232 devices were created. The pin-outs for these classifications were established so that the cable used to connect the two devices would be "straight through" in nature, where each pin is connected to the same pin on the other end of the cable. Pin 1 will connect to pin 1, pin 2 to pin 2, and so on. The PC and the modem in our scenario are examples of these two classifications: 1) the PC represents a Data Terminal Equipment (DTE) and 2) the modem represents the Data Communications Equipment (DCE), respectively. Note: DCE is also referred to as Data Circuit Terminating Equipment. To connect these two devices, simply use a stright-through cable. However to connect two DTE's to each other or two DCE's to each other you would need to use a crossover cable also known as a null modem cable. In the case of this cable, the
pins are reversed on one end - allowing the pins on the two interfaces to connect with the proper pinout on each end.
Universal Serial Bus (USB)
 Figure 2: The ubiquitous USB icon.
Figure 2: The ubiquitous USB icon.
Historically RS-232 has been the most widely implemented serial standard. However due to its limitations such as: speed (only up to 115 Kbps), the fact that it only supports one device per port, and that it requires significant configuration to attach the device, RS-232 has been virtually replaced by USB in all but the most basic applications.
USB 1.1 operates at either 1.5 Mbps or 12 Mbps. USB 2.0 can operate at speeds up to 480 Mbps. USB is capable of supporting up to 126 devices on each port and can be daisy-chained from one device to another. A better solution for larger implementations is to use a USB hub as shown in figure 3.
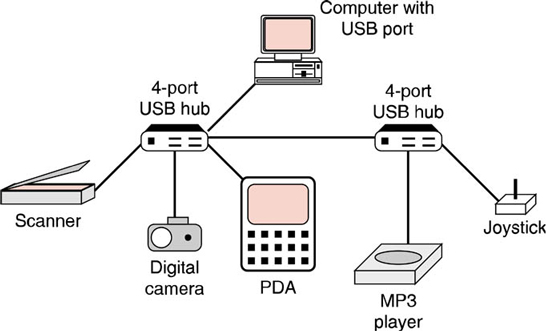 Figure 3: USB peripherals connected to a computer via two 4-port USB hubs.
Figure 3: USB peripherals connected to a computer via two 4-port USB hubs.
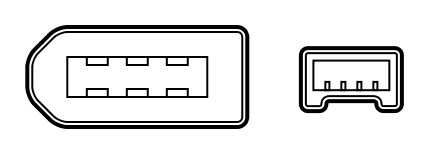
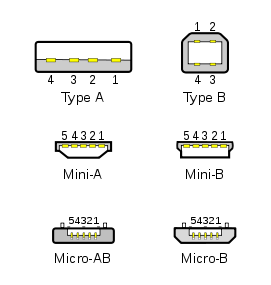 Figure 4: USB connector types
& pinouts.
Figure 4: USB connector types
& pinouts.


IEEE-1394/Firewire

Another high-speed serial standard is IEEE-1394. Originally developed by Texas Instruments and implemented by Apple Computer Inc. as the proprietary Firewire, the interface was standardized by the IEEE in 1995. Sony has trademarked the name i.Link for their implementation of IEEE-1394, and that moniker can now be found on numerous Japanese consumer electronic devices like digital video recorders and cameras.
IEEE-1394 is a multipoint serial bus-based solution. Devices can be added or removed from the live bus. Devices can be daisy-chained or connected to IEEE-1394 hubs. The original IEEE-1394 specification supported data transfer rates up to 400 Mbps and 1394b supports data transfer rates up to 800 Mbps. In addition to using standard asynchronous communications it also includes support for Isochronous communication which guarantees data delivery at a constant, predetermined rate. This allows IEEE-1394 to be used in time critical multimedia solutions. IEEE-1394 supports transmitting data over media up to 100 meters without attenuation. IEEE-1394 uses two different types of connectors 4-wire and 6-wire which can provide power to devices.
 Firewire cable.
Firewire cable.
Parallel Transmission
Parallel transmission is primarily limited to transmission of data within a computer between its various busses, central processing unit, memory, and disk drives. In the past it was commonly used to connect a printer to a computer using a cable that consisted of a DB-25 connector on one end and a Centronics connector on the other end which connected to the printer.

Wireless Technologies
Wireless technologies have become quite popular in recent years. Technologies like infrared and Bluetooth are now commonplace in Personal Area Networks (PANs) and WiFi has
permeated Local Area Network (LAN) environments. Wireless technologies like microwave, cellular, and satellite transceivers can even be found in the larger Campus Area Network (CAN), Metropolitan Area Network (MAN), and Wide Area Network (WAN) environments.
Wireless Personal Area Networks (WPANs)
The idea of personal area networks (PANs) has been around for a long time, a computer's motherboard has long been considered to be a personal area network. With the advent of
wireless technologies like InfraRed and Bluetooth the term wireless
personal area network (WPAN) has been added to the networking nomenclature.
WPAN is based on the standard IEEE 802.15. Examples of WPANs include using a wireless keyboard and/or mouse to provide input to your computer, wireless phones and cellular phones using Bluetooth headsets,
device which send data to a printer with an infrared receiver, remote
controls for digital cameras and camcorders, audio headsets which receive
signals from tablet PCs or other wireless audio transmitters, joysticks and
other peripherals used in conjunction with game boxes, mobile devices
capable of exchanging data via wireless communications and a lot more. Like
the term personal area network (PAN), a WPAN consist of devices which communicate with
each other when positioned at a
relativity short distance from each other.
Infrared

The Infrared Data Association (IrDA) is an international standards body responsible for creating standards that apply to the use of infrared (Ir) light to provide wireless connectivity for devices and/or locations that typically would typically require more traditional wire-based
solutions. IrDA uses Infrared (IR) light to transmit signals between devices and uses a narrow angle (30 degree cone). IrDA is limited to about 1 meter in range and offers a transmission rates ranging from 9600 bps to 4 Mbps. IrDA is considered a point-to-point transmission technology and is limited to line of sight. That is to say that it cannot travel through or around solid objects. The most commonly implemented InfraRed (IR)
PANs are that of an IR equipped laptop communicating with an IR enabled printer. Many TV remote controls and newer Media Center PC's remote controls use infrared technology to communicate with their base equipment. Numerous devices such as PDAs, Cameras, Laptop computers and computer peripherals offer support for IrDA
as well.
Bluetooth

Bluetooth has pretty much all but replaced IrDA as the technology of choice for
WPANs. Originally developed by Erickson, Bluetooth is currently backed by the
Bluetooth Special Interest Group (SIG), a collection of Bluetooth promoters that includes 3COM, IBM, Intel, Microsoft, and Nokia, among others, with the purpose of developing and promoting the use of the Bluetooth technology. Bluetooth operates in the 2.4 to 2.4835 GHz radio frequency (RF) range which makes it
susceptible to interference by cordless telephones, microwave ovens, and
IEEE 802.11b/g Wifi equipped devices. In order to reduce interference caused by devices operating in the same frequency range as Bluetooth, it uses a technique know as Frequency Hop Spread Spectrum (FHSS), which means it is constantly hopping from one frequency to the next within its frequency range. The pattern of frequency hopping must be known by the wireless receiver so that the message can be reconstructed correctly. A given wireless
transceiver's signal is on a given frequency for less than a second. By constantly changing frequency, the transmission tends to be less affected by interference, an especially
desirable characteristic for mobile computing applications.
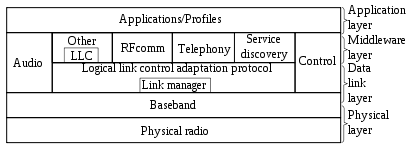 Bluetooth Protocol Stack
Bluetooth Protocol Stack
Bluetooth offers data speeds of up to 1 Mbps over a distance of 10 meters. Unlike IrDA, Bluetooth supports a LAN-like mode where multiple devices can interact with each other. Since Bluetooth does not require line-of-sight it is also much more flexible when compared to IrDA. The key limitations of Bluetooth are security and interference with wireless LANs (IEEE 802.11) devices as stated previously. The fact that Bluetooth doesn't require line-of-sight to communicate cuts both ways: while it makes it possible to use your PDA with your cellular phone that is stashed in your briefcase, it also makes it possible for someone else with a device hidden from view to attempt to gain illicit access to your computing devices. Bluetooth attempts to mitigate the risk through the use of strong authentication and encryption technologies. Because Bluetooth has the same frequency range as IEEE 802.11b wireless networks, simultaneous use of both technologies can greatly affects performance. Devices that use Bluetooth include: wireless keyboards and mice, hands-free cellular phone devices, PDAs, headphones and mobile gaming devices.
Bluetooth Profiles
In order to use Bluetooth technology, a device must be compatible with the subset of Bluetooth profiles (often called services) necessary to use the desired services. A Bluetooth profile is a specification regarding an aspect of Bluetooth-based wireless communication between devices. It resides on top of the Bluetooth Core Specification and (optionally) additional protocols. While the profile may use certain features of the core specification, specific versions of profiles are rarely tied to specific versions of the core specification. For example, there are Hands-Free Profile (HFP) 1.5 implementations using both Bluetooth 2.0 and Bluetooth 1.2 core specifications.
The way a device uses Bluetooth technology depends on its profile capabilities. The profiles provide standards which manufacturers follow to allow devices to use Bluetooth in the intended manner. For the Bluetooth low energy stack according to Bluetooth 4.0 a special set of profiles applies.
At a minimum, each profile specification contains information on the following topics:
-
Dependencies on other formats
-
Suggested user interface formats
-
Specific parts of the Bluetooth protocol stack used by the profile. To perform its task, each profile uses particular options and parameters at each layer of the stack. This may include an outline of the required service record, if appropriate.
List of Bluetooth profiles
Z-Wave

Z-Wave is a wireless communications protocol used primarily for home automation. It is a mesh network using low-energy radio waves to communicate from appliance to appliance, allowing for wireless control of residential appliances and other devices, such as lighting control, security systems, thermostats, windows, locks, swimming pools, and garage door openers. Like other protocols and systems aimed at the home and office automation market, a Z-Wave system can be controlled via the Internet from a smart phone, tablet, or computer, and locally through a smart speaker, wireless keyfob, or wall-mounted panel with a Z-Wave gateway or central control device serving as both the hub controller and portal to the outside. Z-Wave provides the application layer interoperability between home control systems of different manufacturers that are a part of its alliance. There is a growing number of interoperable Z-Wave products; over 1,700 in 2017, and over 2,600 by 2019
The Z-Wave protocol was developed by Zensys, a Danish company based in Copenhagen, in 1999. That year, Zensys introduced a consumer light-control system, which evolved into Z-Wave as a proprietary system on a chip (SoC) home automation protocol on an unlicensed frequency band in the 900 MHz range. Its 100 series chip set was released in 2003, and its 200 series was released in May 2005, with the ZW0201 chip offering high performance at a low cost. Its 500 series chip, also known as Z-Wave Plus, was released in March 2013, with four times the memory, improved wireless range, and improved battery life. The technology began to catch on in North America around 2005, when five companies, including Danfoss, Ingersoll-Rand and Leviton Manufacturing, adopted Z-Wave. They formed the Z-Wave Alliance, whose objective is to promote the use of Z-Wave technology, with all products by companies in the alliance interoperable. In 2005, Bessemer Venture Partners led a $16 million third seed round for Zensys. In May 2006, Intel Capital announced that it was investing in Zensys, a few days after Intel joined the Z-Wave Alliance. In 2008, Zensys received investments from Panasonic, Cisco Systems, Palamon Capital Partners and Sunstone Capital.
Z-Wave was acquired by Sigma Designs in December 2008.[9][13] Following the acquisition, Z-Wave's U.S. headquarters in Fremont, California were merged with Sigma's headquarters in Milpitas, California.[9][14] As part of the changes, the trademark interests in Z-Wave were retained in the United States by Sigma Designs and acquired by a subsidiary of Aeotec Group in Europe.[15][16] On January 23, 2018, Sigma announced it planned to sell the Z-Wave technology and business assets to Silicon Labs for $240 million,[17] and the sale was completed on April 18, 2018.[18]
In 2005, there were six products on the market that used Z-Wave technology. By 2012, as smart home technology was becoming increasingly popular, there were approximately 600 products using Z-Wave technology available in the U.S. As of January 2019, there are over 2,600 Z-Wave certified interoperable products.
Z-Wave Alliance website
Wireless Local Area Networks (WLANs)

Wireless LANs
devices communicate using the WiFi transmission technology which is defined by the IEEE in a specification known as 802.11
and is trademarked by the WiFi Alliance. There have been several generations of the 802.11 standard introduced over the last decade including: 802.11b (11 Mbps), 802.11a (54 Mbps), and 802.11g (also 54 Mbps but offering a further reach than 802.11a). 802.11g is currently the most popular, but soon will be replaced by 802.11n which is currently in the draft stage and will offer speeds up to 540 Mbps.

Wireless devices such as wireless network cards and wireless hubs usually support two wireless modes: AdHoc and Infrastructure. If you simply want two wireless devices to communicate with each other, then both devices should be set to AdHoc mode. If you would like to have multiple wireless devices to be able to access your home or company LAN through a wireless access point (WAP) a.k.a. Access Point (AP), then all of the wireless devices, including the device being used as the access point, should be set to Infrastructure mode. Many businesses like
coffee shops, airports, even city malls offer access to their local area networks and the Internet to the public using WAPs. The term used to refer to these publicly
accessible WAPs is a wireless "hot spot." In some cases users are charged a fee for access to the network, in other cases they are not, it is typically up to the business providing the service the make that decision.
Wireless Access Points (WAPs) and Service Set Identifier (SSIDs)
When in Infrastructure mode (the default mode),
WAPs can be used as access points for other wireless devices to connect to
wired LANs. WAPs broadcast SSIDs which are 32 octet (byte) IDs that enable other wireless devices to "see" and thereby establish a connection with the access point
which has a wired connection to a LAN switch port. For security reasons some network administrators will disable the broadcasting of an SSID by their WAP devices to prevent unwanted users from being able to detect the access points and attempt to hack into them. A hacker technique known as "war games driving" is sometimes used by unscrupulous people who cruise industrial parks and residential neighborhoods looking for WAPs that they can access and use for devious purposes without detection of where the activity is
truly originating from. However, turning off the broadcasting of a WAP's SSID does not prevent the hacker's ability to gain access to the WAP. Anytime a legitimate device connects to the WAP the SSID is transmitted clear text and a hacker can passively "sniff" the wireless network signal and detect the exchange of the SSID between the two devices.
WAP Security
The best way to prevent access to a WAP by unwanted users is to use authentication protocols like RADIUS. Although considered an expensive solution, authentication techniques are commonly used by WiFi hot spots. A simpler more cost effective means of protecting access to a WAP is to secure WAP transmissions. WAP transmissions can be secured by using the less stringent Wireless Encryption Protocol (WEP) which is considered to be weak for most security purposes. Newer second and third generation protocols known as WiFi Protected Access (WPA) versions 1 and 2 are considered very secure when used with strong password protection and are built-in to most of the newer WAPs.
Ad-Hoc Mode
When WAPs are configured for Ad-Hoc mode they can
communicate directly with each other and other wireless devices, but cannot
bridge to wired LANs. Ad-Hoc mode allows you to build an all-wireless LAN,
but performance suffers as the numbers of devices increases, and large
ad-hoc networks can quickly become difficult to manage.
Wireless Regional Area Networks (WRANs)
WRANs are defined by the IEEE's 802.22 standardization committee, it utilizes the unused channels within the range of television frequencies and is not currently in wide use in the United States.
Wireless Wide Area Networks (WWANs)
WWANs use the cellular networks of mobile telecommunications companies to provide access to a multitude of services. Cellular transceivers attached to a computer's PCMCIA or USB port as well as
many brands of cellular phones themselves can be used for Internet access,
transferring email, downloading music and even watching streamed video transmissions. Due to the vast infrastructure made available by mobile telecommunications companies, WWANs are
accessible globally by properly equipped mobile users. WWANs utilize 4G
transmission technologies like Long Term Evolution (LTE) and WiMAX as well
as 3G cellular technologies including: the Universal Telecommunications System
(UMTS) and CDMA2000. The transmission method used by your mobile device's
cellular transceiver must match a transmission method used by your mobile
service provider's cellular towers in order to gain access to their network.
Below is a listing of the more recent transmission methods used by the major
cellular service providers. Many mobile devices, like smartphones and
tablets also support WiFi transmisison standards (IEEE 802.11a/b/g/n) which
are wireless LAN-based transmission methods. Meaning you can use your
company-based or home-based LAN to access your local network in addition to
being able to access the Internet
provided the LAN offers a compatible IEEE 802.11 wireless access point
(WAP). Some telecommunications companies, like AT&T also offer access to
their network by offering WiFi hotspots in some metropolitan areas.
Long Term Evolution (LTE)
The pre-4G technology 3GPP Long Term Evolution (LTE) is often branded "4G-LTE", but the first LTE release does not fully comply with the
International Mobile Telecommunications Advanced (IMT-Advanced) requirements. LTE has a theoretical net bit rate capacity of up to 100 Mbit/s in the downlink and 50 Mbit/s in the uplink if a 20 MHz channel is used — and more if multiple-input multiple-output (MIMO), i.e. antenna arrays, are used.
The physical radio interface was at an early stage named High Speed OFDM Packet Access (HSOPA), now named Evolved UMTS Terrestrial Radio Access (E-UTRA). The first LTE USB dongles do not support any other radio interface.
The world's first publicly available LTE service was opened in the two Scandinavian capitals Stockholm (Ericsson and Nokia Siemens Networks systems) and Oslo (a Huawei system) on 14 December 2009, and branded 4G. The user terminals were manufactured by Samsung.
Currently, the three publicly available LTE services in the United States
are provided by MetroPCS (the first to offer LTE in the U.S. in 2010), Verizon Wireless, and AT&T. As of April 2012, US
Cellular also offers 4G LTE. Sprint Nextel has also stated it's considering switching from
WiMAX to LTE in early 2012.
LTE-Advanced
LTE Advanced (Long-term-evolution Advanced) is a candidate
for IMT-Advanced standard, formally submitted by the 3GPP organization to
ITU-T in the fall 2009, and expected to be released in 2012. The target of
3GPP LTE Advanced
is to reach and surpass the ITU requirements. LTE Advanced is essentially an enhancement to LTE. It is not a new technology but rather an improvement on the existing LTE network. This upgrade path makes it more cost effective for vendors to offer LTE and then upgrade to LTE Advanced which is similar to the upgrade from WCDMA to HSPA. LTE and LTE Advanced will also make use of additional spectrum and multiplexing to allow it to achieve higher data speeds. Coordinated Multi-point Transmission will also allow more system capacity to help handle the enhanced data speeds. Release 10 of LTE is expected to achieve the IMT Advanced speeds
of 1 Gbps peak download and 500 Mbps peak upload. Release 8 currently supports up to 300 Mbit/s download speeds which is
obviously still short of the IMT-Advanced standards.
5G
In telecommunications, 5G is the fifth generation of cellular network technology, which mobile operators began deploying worldwide in 2019 as the successor to 4G. 5G is based on standards defined by the International Telecommunication Union (ITU) under the IMT-2020 requirements, which outline performance targets for speed, latency, and connectivity to support advanced use cases.
Like their predecessors, 5G networks are cellular networks, in which the service area is divided into small geographical areas called cells. All 5G wireless devices in a cell are connected to the Internet and the telephone network by radio waves through a base station and antennae in the cell. The new networks offer not only higher download speeds, with a peak speed of 10 gigabits per second (Gbit/s) when there is only one user in the network, but also significantly lower latency, enabling near-instantaneous communication.[1] 5G networks have higher bandwidth, allowing them to connect more devices simultaneously and improving the quality of Internet services in crowded areas.[2] These features make 5G particularly suited for applications requiring real-time data exchange, such as extended reality (XR), autonomous vehicles, remote surgery, and industrial automation. Additionally, the increased bandwidth is expected to drive the adoption of 5G as a general Internet service provider (ISP), particularly through fixed wireless access (FWA), competing with existing technologies such as cable Internet, while also facilitating new applications in the Internet of Things (IoT) and machine-to-machine communication.
The increased bandwidth and lower latency of 5G networks enable highly responsive, large-scale IoT deployments, supporting diverse applications such as smart cities, connected infrastructure, industrial IoT, and automated manufacturing processes. Unlike 4G, which was primarily designed for mobile broadband, 5G can handle millions of IoT devices with stringent performance requirements, such as real-time sensor data processing and edge computing.
5G networks also extend beyond terrestrial infrastructure, incorporating non-terrestrial networks (NTN) such as satellites and high-altitude platforms, to provide global coverage, including remote and underserved areas.
Despite its performance improvements, 5G deployment faces challenges such as significant infrastructure investment, spectrum allocation, security risks, and concerns about energy efficiency and environmental impact associated with the use of higher frequency bands. However, it is expected to drive advancements in sectors like healthcare, transportation, and entertainment.
Devices with 4G capabilities are not compatible with 5G networks due to the lack of necessary hardware to support the significant changes in network architecture and the higher frequencies used in 5G.
WiMAX

Worldwide
Interoperability for Microwave Access (WiMAX) uses microwave technology to transmit and receive
and is best suited for Metropolitan Area Network (MAN) applications. WiMAX
is defined by the IEEE's 802.16 standards committee and is designed to
replace DSL and cable as an option for high-speed access in the "last mile"
of data and telecommunications. The last mile or "local loop" is essentially
the connection made by a business or residential subscriber to the
telecommunications company's central office. Although fiber optics offers the highest transfer rates in these situations, the advantage of WiMAX is, of course, mobility.
WiMAX offers peak data rates of 128 Mbit/s downlink and 56 Mbit/s uplink over 20 MHz wide channels. Sprint Nextel has deployed WiMAX technology which it has labeled 4G as of October 2008. It is currently deploying to additional markets and is the first US carrier to offer a WiMAX phone.
Caution:
Sprint Nextel's 4G coverage area is usually limited to major metropolitan areas. Be sure to
check your cell provider's coverage map before purchasing a 4G phone because
you may live in an area which does not offer 4G service. In the case of
Sprint Nextel, if you buy a 4G phone but live in an area that has no 4G coverage
you will still be required to pay an extra $10 per month for the 4G service
even though you don't have access to their 4G network.
HTC's EVO 4G phone supports the WiMAX technology.
Ultra Mobile Broadband (UMB) (formerly EV-DO Rev. C)
UMB was the brand name for a discontinued 4G project within the
3GPP2 standardization group to improve the CDMA2000 mobile phone standard for next generation applications and requirements. In November 2008, Qualcomm, UMB's lead sponsor, announced it was ending development of the technology,
favoring LTE instead. The objective was to achieve data speeds over 275 Mbit/s downstream and over 75 Mbit/s upstream.
Universal Telecommunications System (UMTS)
In the U.S. the 1710 – 1755 MHz bandwidth is used for uplinks and the 2110 – 2155 MHz bandwidth is used for downlinks. It offers data transfer rates of 14 Mbps theoretical, but in actuality 2 Mbps stationary, 384 Kbps moving downstream and 100 Kbps moving upstream. In the U.S. UMTS is primarily used by AT&T and
T-Mobile for their mobile network services.
Evolution Data-Optimized (EVDO) revision B
Primarily used by Sprint and Verizon in the U.S., EV-DO is a 3G digital radio technology that is based on Code Division Multiple Access (CDMA2000) technology which has an advantage over its competitors in that more cell phones can be served by fewer cell towers. The drawback to CDMA is that the
technology is patented by Qualcomm which charges a usage fee for each device that uses its technology. It is defined to operate at 450 MHz, 700 MHz, 800 MHz, 900 MHz, 1700 MHz, 1800 MHz, 1900 MHz, and 2100
MHz EVDO revision A offers similar data rates to that of UMTS, but revision B offers 4.9 Mbps on the downlink.
Wide Area Network and Internet Access Technologies
Most homes and Businesses these days have access to the Internet. Businesses use the Internet as a means to connect remote sights to one another and to allow their employees to access the company network from home or while on the road. It wasn't too long ago that it was common for companies to pay for "frame Relay" or "X.25" services to make these connections. Many
companies still do, as Frame Relay and X.25 are considered to be more secure Wise Area Network services than the publicly
assessable Internet network of telecommunications connections. For the most part, telecommunications companies provide the physical pathways that allow homes to connect to business, businesses to connect to remote sites, or businesses to connect to other businesses. Telecommunication companies offer a wide variety of connection types from dial-up technologies including the Integrated Digital Services Network (ISDN), to Digital Subscriber Lines (DSL), and higher conditioned and more
expensive service lines like T1s and T3s. Cable companies also are now able to offer their customers Wide Area Network services usually for the
purposes of accessing the Internet.
Internet Service Providers (ISPs)
In addition to needing a physical link that allows businesses to connect to other businesses, those that utilize the Internet also need what is called an Internet Service Provider (ISP). An ISP is a company that has has their routers connected directly to one of the Internet's backbone of routers, called Internet Exchange Points (IXPs), or to other ISPs who have direct links to the backbone of Internet routers. It is extremely expensive for companies to be directly connected to an Internet IXP, millions of dollars, and so again it is mainly the largest telecommunications companies who possess direct access to an Internet IXP. Click here to read a brief history of the Internet as well as more information about ISP and IXPs.
Dial-Up Modems

Dial-up modems convert a sending computer's digital output to an analog wave pattern that is compatible with analog phone lines, this process is called "modulation." On the receiving end the analog waveforms are converted back into digital for processing by the receiving computer, this is called "Demodualtion." This is how dial-up modems get their name, by combining the first two letters "mo" from modulation with the first three letters "dem" in demodualtion to form "modem"
Digital Subscriber Line (DSL)
Web pages seem to be ever increasing in size with the addition of multimedia elements like streaming video and audio, plus with the addition of new technologies like voice over IP, dial-up modems have become to slow to meet the needs of the Internet consumer. To accomodate the needs of the modern day Internet customer, newer broadband access technologies have been developed. Broadband has many definitions, but the simplest is to consider any access technology that provides access to the Internet at greater than 56 Kbps to be braodband technology.
DSL use the same physical local loop connection as the local telephone service used in POTS (Plain Old Telephone Service). When a local loop is used for DSL, frequency division multiplexing is used to separate the existing voice service from the DSL service. Because the downstream badnwidth is larger than the upstream link, this type of DSL is referred to as "aDSL" (Asymmetric DSL).

In order to support DSL service, additional equipment must be installed, a DSL Access Multiplexer (DSLAM) at the CO (Central Office) and a DSL modem at the customer's premises.

The DSL modem works like the dial-up modems discussed earlier in that it takes digital signals from your computer and converts it to analog signals for transmission over the local loop to the central office using the same digital to analog modulation technologies as a dial-up modem. The key difference is that the DSL modem doesn't need to "dial up" the central office every time you want to connect to the Internet.

Cable Modems
In addition to gaining access to the Internet using your local phone company, your local cable company can provide you with access as well. The same line that supplies your home or business with television service can also provide Internet service. In the beginning cable company lines could only carry signals from the cable company office to the subscriber; a telephone line had to be used to send from the subscriber back out to the Internet. Another early drawback to cable systems was their shared bandwidth. All homes in a neighborhood shared the same trunk line to access the Internet, resulting in decreased performance with each additional subscriber using the line at the same time you were. Now days, cable companies use digital lines which are capable of transmitting in both directions enabling them to be more competitive with the telecommunication companies.
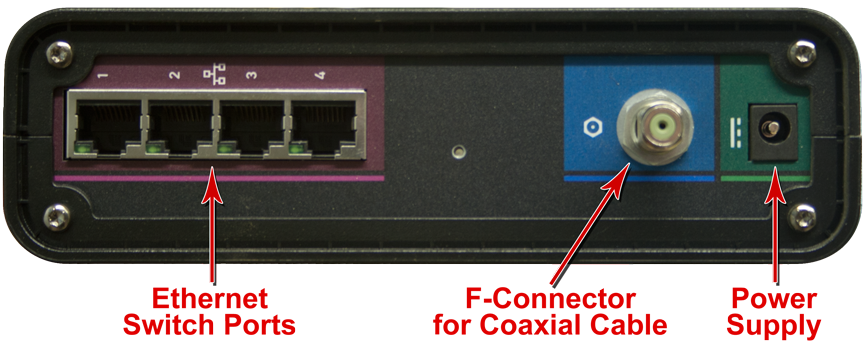
Cabling
 Figure 10: Illustration of an Unshielded Twisted Pair wiring cross-section.
Figure 10: Illustration of an Unshielded Twisted Pair wiring cross-section.
 Figure 11: Unshielded twisted pair (UTP) Cat 5e cabling.
Figure 11: Unshielded twisted pair (UTP) Cat 5e cabling.
 Figure 12: STP cross-section.
Figure 12: STP cross-section.
 Figure 13: Shielded twisted pair (STP) cabling.
Figure 13: Shielded twisted pair (STP) cabling.